Five years ago, the EU ordered a privacy ruling enabling internet users to have certain information about them removed from search results. In other words, specific information relating to a person, entity or a company can be delisted internet across, depending on a set of specific criteria.
Naturally, the entity most impacted by the legislation was Google, the all-encompasing, larger than life search engine. Virtually anyone can request delisting of an URL that contains information, in their name by submitting a form where they state the reason for the delisting that is later analyzed for approval.

Credits: Google G-NEO remix by Katt Phatt™
What is the right to be forgotten?
The right to be forgotten or otherwise colloquially known as “search delisting” is basically a right to privacy “whereby individuals can request that search engines such as Google, Bing, and Yahoo delist URLs from across the Internet that contain “inaccurate, inadequate, irrelevant, or excessive” information surfaced by queries containing the name of the requester [7]. Critically, the ruling requires that search engine operators make the determination for whether an individual’s right to privacy outweighs the public’s right to access lawful information when delisting URLs.” (as stated by Google, read the whole document here)
Search delisting by the numbers
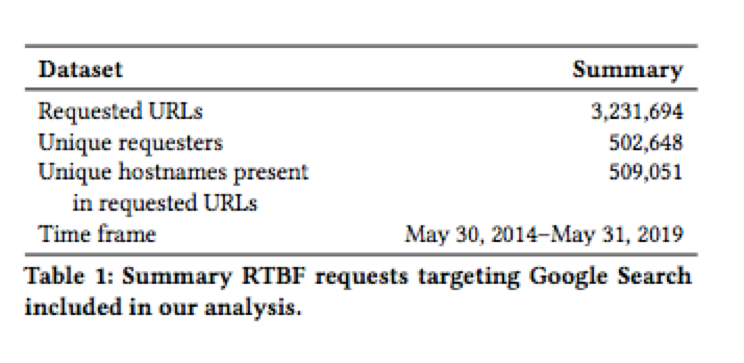
5 years after, more than 3 million delisting requests have been made since the law first came into effect on May 2014.
The scope of the ruling however, is still a question for debate about how search engines discern and resolve these requests, sometimes standing between a rock and a hard place, between the right to privacy and censorship.
First of all, the data set includes all requests filed with Google Search from May 30, 2014 to May 31, 2019.
Who wants to exercise the right to be forgotten more?
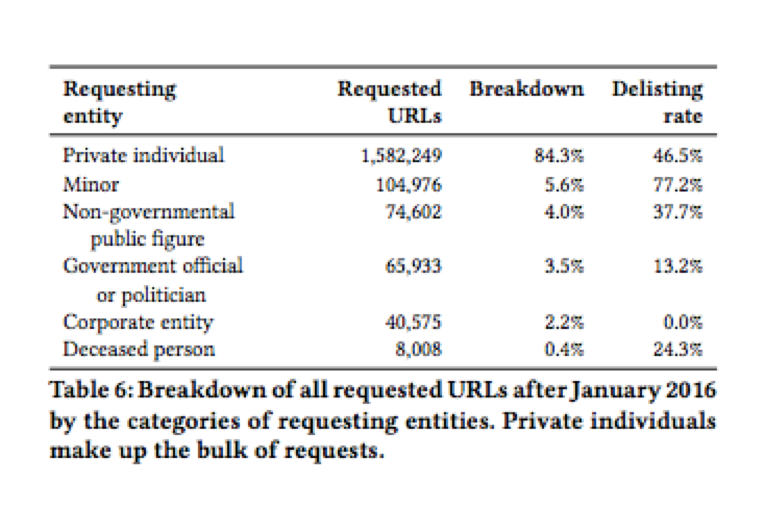
Out of the total requesting entities, no less than 84.3% are private individuals.
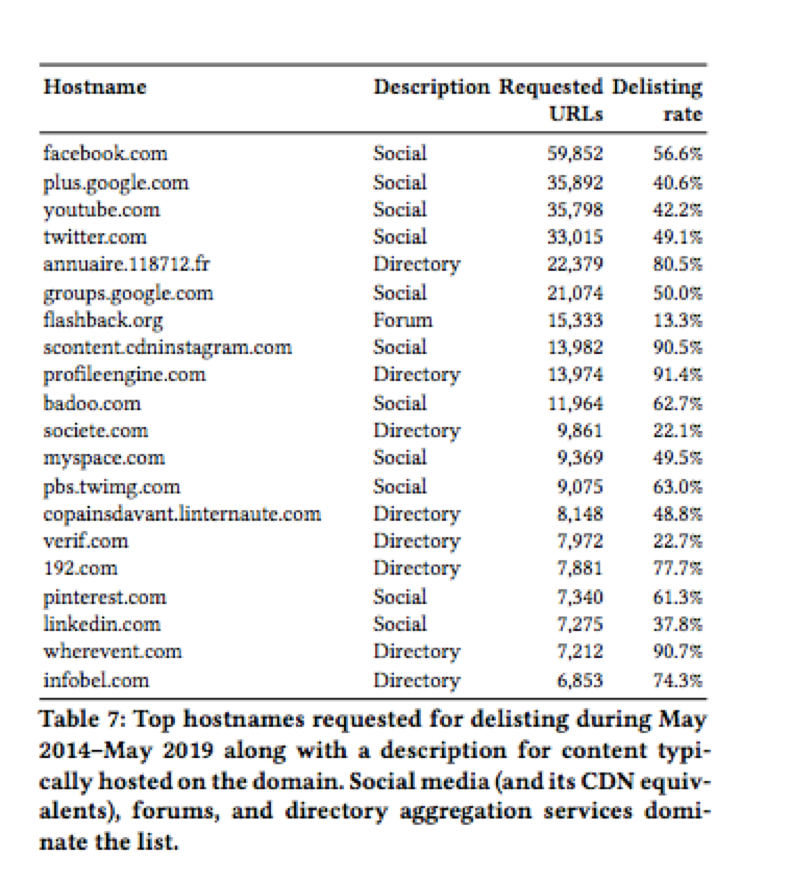
As far as hostnames go, half are social networks and forums, while the other half include directory sites that aggregate contact details and personal content from other sites such as Profile Engine.
What does it all mean?
Our Google Activity Should Be Nobody’s Business. Literally. And the EU directive is a good step in the right direction, as far as it does not border on the illegal or censorship. Beyond the matter at hand, there are businesses taking place in the search bar and far beyond, not only pay per click systems but extensive data collection of all your Google activity, is at the basis of high profiling well.. you, with a big emphasis on your shopping preferences or political affiliation.
Taking a privacy stance when it comes to using the internet is the new “drink responsibly”, so prior to feeling entitled to a private life while online, let’s just start with a clear mind in recognizing how much of what we put out there is actually in our power, slash hands, slash keyboards.
And yet another important amendment before you go, let’s also rise above the inclination of brand association, of trying to find a scape goat. Meaning that regardless if it’s Facebook, Google or big telecom names like say Verizon or Comcast, whichever the brand hype media is taking a stand towards, let’s just admit that privacy breaches and privacy concerns are virtually everywhere. High and low.
So, with realistic expectations of what the online environment means today from two main perspectives as informational medium and marketing tool, we can manage to reach a clearer understanding of what to do in order to preserve privacy, while enjoying all of the perks the online world brings to the table.
For enhanced privacy, people are also turning to VPNs to reclaim or preserve online freedom and privacy and we strongly advise that you do the same.
No longer an exotic tool,VPNs are now entering the mainstream and given the context it’s easy to understand why.
Simply put, when you’re using aVPN, all your data travels through a tunnel encrypted from end to end. In other words, not even your ISP will be able make sense of your data, since you’ll have all your online data happen elsewhere, not going through your ISP servers and encrypted all the while.