Photo Credit: thehackernews.com
Last Friday, WannaCry “ransomware” cyber attach struck globally in what has become one of the fastest –spreading extortion campaigns on record.
The virus infected more than 300,000 machines in 150 countries since Friday and the victim numbers continue to grow. In this very moment, someone could be clicking a link or activating macros in a malicious document.
A few seconds later, the entire hard disk content, personal files and sensitive information, everything including cloud storage accounts synced with PCs could be locked for good. Or for a good tidy ransom. A pop up in bad graphic could then appear on screen asking for “cold hard cash” in return for a decryption key.

Photo Credit: heimdalsecurity.com
If this is what you’re experiencing, well then tough luck. You’re device has been infected with WannaCry. Guess who’s not crying? All those people who are using a VPN. That thing you could never quite grasp the importance of. But wait! How is this even possible, how frequent these things can happen and could they happen to me? you ask.
Ok, let’s give some context and background to the story for clarity.
The first ransomware attack struck in 1989, almost 3 decades ago. It’s hard to fathom now, but the virus spread via floppy disks and involved sending $189 to a post office box in Panama. AIDS Trojan was the WannaCry ransomware from back in the day.
The following graph shows just how intricate this type of malware has become, in the past 10 years, eased by the appearance of Bitcoin and the evolution of encryption algorithms. Starting out as a minor threat of cyber vandalism, this type of cyber crime is now a high scale money making machine.

Photo Credit: heimdalsecurity.com
To name the most recent inglorious attack of this nature we can name the bank heist of no less than $81 million stolen from a Bangladesh bank, that took place only last year.
But ransomware attacks are believed to have broader implications in much more than just making money, as they have been used as tool in cyber battles of political substratum, the attacks on Sony Pictures Entertainment – in retaliation for the comedy film “The Interview” is a telling example. The hacker attack was aimed at Sony Pictures for the satirical comedy directed by Seth Rogen, that involved a plot to assassinate North Korean leader Kim Jong-un. Who knew a Seth Rogen film could get this “inflammable”, right? Well if we think that the attack is believed to being launched by Lazarus Group, allegedly a North Korean run hacking operation is starting to make sense.

Photo Credit: globalriskinsights.com
Technical clues found in the code of WannaCry ransomware by researchers could link to the same North Korean group. However, no conclusive proves have been found for a clear conclusion in any of the aforementioned attacks.

Photo Credit: thehackernews.com
If in the case of Sony Pictures cyber attack, the goal was to prevent the release of The Interview, a film that mocked a North Korean leader, in contrast WannaCry was wildly random infecting everything it could.
WannaCry didn’t seem to have a pecuniary goal, with more than 200,000 machines infected and around $70,000 paid in ransoms, it’s a terrible return.
Analysts are now turning to another hypothesis, maybe the ransom was a distraction for a political goal that has yet to clearly surface.
And here’s were things get really confusing and could take a really steep turn for the left so brace yourself for what I will reveal in the following of what the political implication could be
Brad Smith, President of Microsoft Corp, confirmed in a blog post on Sunday that WannaCry attack made use of a hacking tool developed by the NSA (US National Security Agency) that had leaked online in April. This pours fuel on the long running debate over espionage and cyber warfare conduct and software flaws best kept secrets.

Photo Credit: www.ft.com
Elevating the subject far beyond the immediate need to improve a computer defenses, the WannaCry attack has turned into a political debate in Europe and the United States with discussion of the role national governments play.
Since China was among the worst hit, it seemed unlikely to some that Lazarus was behind all this, as antagonizing North Korea strongest ally would not hold as a good strategy. Having been speculated as having an implication, Russia denied all accusations, but Putin did not waste the change to draw attention on the NSA in the light of Smith’s revealing on the topic.
If this story is not in the realm of a true Matrix scenario unfolding, then I don’t know what is. But just as Neo is looking for a way to Zion, you too could be wondering for the same path.

Photo Credit: fliwave.com
These days data that is a day old can usually be recovered, but potentially losing real time data for even 24 hours can produce massive damage for a company, for example, just like a lack of oxygen to the brain.
Unless you have a back up, which companies usually have, but most people don’t, you can be faced with a cyber attack that could damage tones of done work,
memories stored on picture or film or well put together playlists that took years to build.
Here are the most common infection methods used by cybercriminals.
- Spam email campaignsthat contain malicious links or attachments
- Security exploits in vulnerable software;
- Internet traffic redirects to malicious websites;
- Legitimate websites that have malicious code injectedin their web pages;
- Drive-by downloads;
- SMS messages (when targeting mobile devices);
- Botnets;
- Self-propagation(spreading from one infected computer to another)
SO WHAT IS THE SOLUTION?
In all cases prevention is the best thing you can do. Considering how intricate these attacks are in the large scheme of things is better to take the matter into your own hands and not wait for government to regulate. Besides, do you really trust the government with your personal data? Just a question.
Remember we talked about VPNs at the beginning. Did you know that having a VPN in place can protect your computer from remote attackers? All attacks will stop into the VPN vendor.
Having a robust VPN to encrypt your personal data is nowadays, the only way to Zion.

Photo Credit: ifc.com
Across the world, businesses use VPNs to connect to remote data centers, or for employees to connect remotely to the physical network of their workplace, while individuals can use VPNs to get access to network resources when they’re not physically on the same LAN (local area network), or as a method for securing and encrypting their information from the potential liabilities that lie ahead once exposed to unsecured networks such as public WiFis or hotspots.
REASONS YOU SHOULD START USING A VPN APP. NOW:
- PROTECTS YOUR DATA FROM REMOTE ATTACKERS
your internal data, sites, git repositories, banking credentials and all information will be coated in multiple layers of encryption;
- REMOTE ACCESS
as IT is being challenged to enable safe access to employees remotely by providing mobile VPN, secure email, encrypted containers and virtual desktop infrastructure (VDI), living outside the data security paradigm is simply not smart anymore, whether we’re talking about corporate or personal data;
- IP CAMOUFLAGE
A simple VPN download gets you a new location identity so that you can use geographically dispersed resources;
- BYPASSING FILTERS AND GEORESTRICTIONS
Bypassing Internet censorship in countries where censorship is applied;
- SHARING FILES
You can share files and sensitive information inside a secured group away from prying eyes;
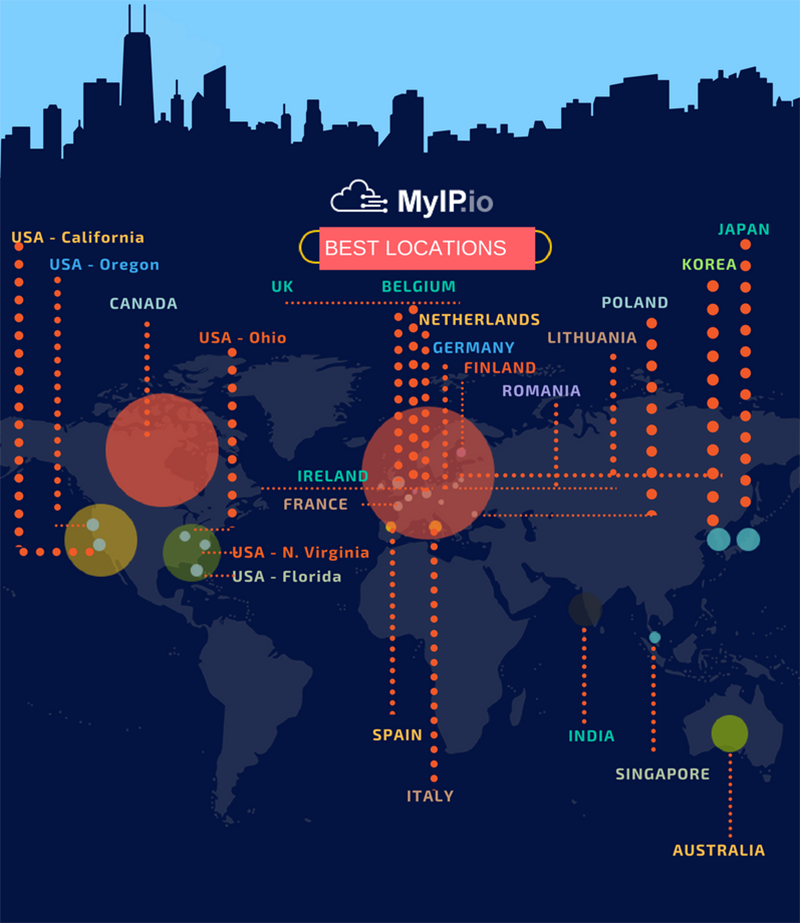
MyIP.io is a self-managed VPN network platform, delivering fast, secure and reliable VPN service , designed with the professional focus in mind. Our platform caters to a wide demographic through three channeled directions:Personal,Dedicated and Business, so it makes for a wonderful choice for corporate or personal use at the same time.
Engineered as a global platform,MyIP.io is a VPN service provider committed to developing applications and services that preserve an open and secure Internet experience while respecting user privacy.
“MyIP.io is the result of the craftsmanship of our engineers, with many years of experience supporting large-scale, custom deployments for businesses , telecommunications companies, multi-service operators and enterprises.” Dave Wilson, CEO My IP.io